A number of different assessment methodologies have been and are being applied to CCSCarbon dioxide CaptureThe separation of carbon dioxide from other gases before it is emitted to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) and Storage-related projects. The main methodologies being used are: (a) scenarioA plausible description of the future based on an internally consistent set of assumptions about key relationships and driving forces; note that scenarios are neither predictions nor forecasts analysis, analyzing how a CO2Carbon dioxide storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) system might evolve in particular in terms of CO2Carbon dioxide migrationThe movement of fluids in reservoir rocks/leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column, (b) fault(geology) A surface at which strata are no longer continuous, but are found displaced / event tree analysis, to evaluate as a combination of possible steps the network of pathways for CO2Carbon dioxide release and migrationThe movement of fluids in reservoir rocks starting from thestorage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) reservoirA subsurface body of rock with sufficient porosityMeasure for the amount of pore spaceSpace between rock or sediment grains that can contain fluids in a rock and permeabilityAbility to flow or transmit fluids through a porous solid such as rock to store and transmit fluids and ending at a particular point of interest, (c) expert judgment, to derive from relevant experience and expertise in a specific area, the likelihood of CO2Carbon dioxide leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column, (d) screening-level analysis, which can be useful to compare safety characteristics of different sites based on expert opinion (Stenhouse et al., 2009). In parallel with methodologies, a variety of approaches are available for mathematical modecoing, which can be classified under three general categories: (a) numerical models, which use discretization methods to model detailed processes describing the system evolution over space and time, (b) analytical / semi-analytical models, which are mathematical models in which the solution to the equations used to describe changes in the system can be expressed as an analytical or semi-analytical function, typically as a function of time in the case of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event for CCSCarbon dioxide CaptureThe separation of carbon dioxide from other gases before it is emitted to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) and Storage projects, and (c) coCarbon monoxidempartment or mixing-cell models, representing a large family of models, where the model comprises a series of individual compartments representing different physical domains of the total storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) system. All of the above-mentioned models can be run deterministically or probabilistically (Stenhouse et al., 2009).
RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event methodologies are generally classified in two main groups: qualitative and quantitative.
-
Qualitative RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event does not provide concrete or numerical results. In case of a lack of data and/or specific knowledge, time and expertise, qualitative riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event may be sufficient and more effective. Among the most common qualitative methods are the Features, Events, and Processes (FEP), and the Vulnerability Evaluation Framework (VEF).
-
Quantitative Methods are used in wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injectionThe process of using pressure to force fluids down wells of fluids-known systems where the level of uncertainty is relatively low. Two main kinds of methods belong to this group: Deterministic RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event (DRA) and Probabilistic RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event (PRA). DRA does not handle uncertainty, but is useful in determining trends due to its single parameter variation. It gives very accurate results when the input parameters are exactly known. PRA, on the other hand, can statistically quantify the uncertainty associated with parameters describing the processes in deterministic models. PRA is the most preferable method of assessing long-term riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event in complex systems (Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
Table 6.1 summarizes the main characteristics of some riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event methods. It should be noted that some methods are not considered in this table, e.g. Preliminary Hazard Analysis (PHA), Failure Mode and Effects Analysis (FMEA), Fault(geology) A surface at which strata are no longer continuous, but are found displaced Tree Analysis (FTA) and Fuzzy Logic.
| 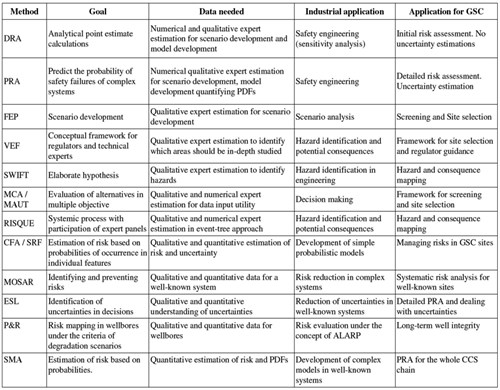
Tab. 6-1: RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event Methods (Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more). |
The Features, Events and Processes (FEP) method consists of listing relevant factors that describe the current state and possible future evolution of a site. The FEP analysis is useful in the licensing and certificationIn the context of carbon trading, certifying that a project achieves a quantified reduction in emissions over a given period stages of project development..
The Vulnerability Evaluation Framework (VEF) is a qualitative method which systematically identifies conditions that could increase or decrease the potential for adverse impacts (i.e., susceptibility to consequences). The VEF (EPA, 20082008 - USEPAVulnerability Evaluation Framework for Geologic Sequestration of Carbon Dioxidesee more) is not designed as a site selection tool, it does not aim to establish performance standards, or to specify data requirements. It is a conceptual framework designed to help regulators and technical experts in framing specific considerations and identifying areas that require design evaluation, specific riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event, monitoringMeasurement and surveillance activities necessary for ensuring safe and reliable operation of a CGS project (storage integrity), and for estimating emission reductions, and management (Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
The RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event Identification and Strategy using Quantitative Evaluation (RISQUE) proposed by Bowden and Rigg, 20042004 - A. R. Bowden and A. RiggAssessing Risk in CO2 Storage Projectssee more is a systematic quantitative process based on the judgment of a panel of experts. It delivers a transparent riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event in a process that can interface with the wider community and allow stakeholders to assess whether the CO2Carbon dioxide injectionThe process of using pressure to force fluids down wells process is safe, measurable and verifiable. It has been applied in Australia, under the GEODISC research program, to assess the riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event posed by conceptual CO2Carbon dioxide injectionThe process of using pressure to force fluids down wells in four selected areas (Dongara, Petrel, Gippsland, and Carnavarcon). The approach relies on quantitative techniques to characterize Risks in terms of both likelihood of identified riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event events occurring (such as CO2Carbon dioxide escape and inadequate injectivityA measure of the rate at which a quantity of fluid can be injected into a well into the storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) site) and consequences (such as environmental damage and loss of life). It coCarbon monoxidensists in five stages:
Stage 1- Establishing the context, i.e., assessment of the nature of the activities and potential impacts,
Stage 2- RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event identification,
Stage 3 - RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event analysis, i.e., quantification and modeling of probabilities and COnsequences for each substantive riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event event,
Stage 4 - Development of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event management strategy, i.e., defining and evaluating options for action plans to treat key riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event events,
Stage 5 - Implementation of the riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event management strategy (Bowden and Rigg, 20042004 - A. R. Bowden and A. RiggAssessing Risk in CO2 Storage Projectssee more).
RISQUE methodology in conjunction with a modified Delphi approach was proposed for assessing and quantifying riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event in CO2Carbon dioxide geological storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) projects aiming at the reductionThe gain of one or more electrons by an atom, molecule, or ion of uncertainties. The RISQUE process does not routinely include a continual and progressive technology riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event component but the modified Delphi process could address this potential need. The RISQUE method addresses the risks but in a linear scheme, whereas in complex programmatic settings, risks are considered in a non-linear scheme, chosen by interveners or stakeholders. The modified Delphi technique, when planned and implemented wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injectionThe process of using pressure to force fluids down wells of fluids, can bring all elements of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event, presumably from the non-linear 'riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event-space' into a controlled input for the RISQUE process. It quantifies and qualifies the risks perceived by others into a set of consensus risks, in a re-iterative agreement process, and weight those factors against the expertpanel of the RISQUE process. As the RISQUE process proceeds, the Delphi re-iterative process continues using smaller subgroups and continued quantified and qualified weighted input (Wyatt et al., 2009).
The Structured What-If Technique (SWIFT) is a form of Delphi riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event analysis used for qualitative hazard identification that was attempted by Vendrig et al., 2003, who identified major hazards through a "Structured What-If Technique" involving an expert panel (CSLF, 20092009 - CSLFPhase I Final Report from CSLF Risk Assessment Task Forcesee more). The method was developed as an efficient alternative to the Hazard and Operability (HAZOP) technique and to the Failure Modes and Effects Analysis (FMEA) for providing highly effective hazard identification in situations and systems where none of them were adequate. It consists of a series of "what-if…?" or "How could…?" questions to identify situations, issues or threats of potential harm. There is no single standard approach to SWIFT which is flexible and has to be modified to suit each individual application (Vendrig et al., 20032003 - M. Vendrig, J. Spouge and A. BirdRisk analysis of the geological sequestration of carbon dioxidesee more; Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
The CertificationIn the context of carbon trading, certifying that a project achieves a quantified reduction in emissions over a given period Framework (CF or CFA) is a simple riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event approach for evaluating CO2Carbon dioxide and brine leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event at GCS sites (Oldenburg et al., 20092009 - C. M. Oldenburg, S. L. Bryant and J.-P. NicotCertification Framework Based on Effective Trapping for Geologic Carbon Sequestrationsee more). It is similar to VEF, but it adds values for the leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column probability (Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more). Its purpose is to provide a framework for project proponents, regulators, and the public to analyse the risks of geologic CO2Carbon dioxide storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere in a simple and transparent way to certify start-up and decommissioning of storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere sites. The CF currently emphasizes leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event associated with subsurface processes and excludes compression, transportation, and injectionThe process of using pressure to force fluids down wells-wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column risks. It is designed to be simple by using (a) proxy concentrations or fluxes for quantifying impact rather than complicated exposure functions, (b) list of pre-computed CO2Carbon dioxide injectionThe process of using pressure to force fluids down wells results, and (c) simple framework for calculating leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event. For quantification of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event, the system is divided into compartments that can be subsurface (hydrocarbon reservoirs or underground sources of water), at surface (local sites where leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column occurs) and distant sites (Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more). The CF approach has to be based on a clear and precise terminology in order to communicate to the full spectrum of stakeholders:
-
Effective trapping(CO2Carbon dioxide) ContainmentRestriction of the movement of a fluid to a designated volume (e.g. reservoir) or immobilisation of CO2Carbon dioxide, there are four main trapping mechanisms: structural or stratigraphicThe order and relative position of geological strata trapping; residual CO2Carbon dioxide trapping (capillary trappingImmobilisation of a fraction of in-situ fluids by capillary forces) by capillary forces; solubility trappingA process in which fluids are retained by dissolution in liquids naturally present by dissolution of CO2Carbon dioxide in resident formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it fluids forming a non-buoyant fluid; and mineral trapping where CO2Carbon dioxide is absorbed by solid minerals present in the storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) volume (proposed overarching requirement for safety and effectiveness),
-
Storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) region (3D volume of the subsurface intended to contain injected CO2Carbon dioxide),
-
Leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column,
-
Compartment (region containing vulnerable entities, e.g. environment and resources),
-
Impact,
-
RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event,
-
CO2Carbon dioxide leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event (riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event to compartments arising from CO2Carbon dioxide migrationThe movement of fluids in reservoir rocks, i.e. the product of the probability of intersection of leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column paths with compartments (Oldenburg et al., 20092009 - C. M. Oldenburg, S. L. Bryant and J.-P. NicotCertification Framework Based on Effective Trapping for Geologic Carbon Sequestrationsee more; Dodds et al., 2011).
In the CF, impacts occur to compartments such as HMR (Hydrocarbon and Mineral Resource), HS (Health and Safety), USDW (Underground SourceAny process, activity or mechanism that releases a greenhouse gas, an aerosol, or a precursor thereof into the atmosphere of Drinking Water), NSE (Near-Surface Environment), and ECA (Emission Credits and AtmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%)). Wells and faults are assumed to be the only potential leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column conduits. Fig. 6-4 shows the CF conceptualization of the system into sourceAny process, activity or mechanism that releases a greenhouse gas, an aerosol, or a precursor thereof into the atmosphere, conduits and compartments (left-hand side), and a flow chart of the general CF logic and inputs and output (right-hand side). A similar method to the CF approach is the Screening and Ranking Framework (SRF) which is based on the assumption that if the primary sealAn impermeable rock that forms a barrier above and around a reservoir such that fluids are held in the reservoir or containmentRestriction of the movement of a fluid to a designated volume (e.g. reservoir) leaks, the second sealAn impermeable rock that forms a barrier above and around a reservoir such that fluids are held in the reservoir will act. If the second sealAn impermeable rock that forms a barrier above and around a reservoir such that fluids are held in the reservoir fails, then the leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column will be attenuated or dispersed (Oldenburg, 2008; Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
| 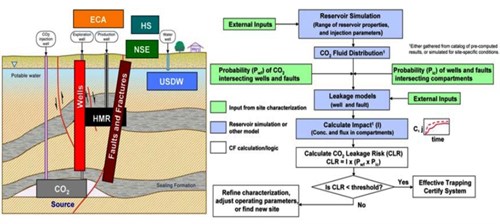
Fig. 6-4: Generic schematic of compartments and conduits in the CF (left-hand side), and flow chart of the CF approach (right-hand side) (Oldenburg et al., 20092009 - C. M. Oldenburg, S. L. Bryant and J.-P. NicotCertification Framework Based on Effective Trapping for Geologic Carbon Sequestrationsee more). |
The Multi-Criteria Assessment (MCA) covers a variety of non-monetary evaluation techniques sharing a basic framework under which a number of alternatives can be scored against a series of defined or fixed criteria. This list of criteria is proposed according to the fundamental goals of the CGSCO2 Geological Storage; Injection accompanied by storage of CO2 streams in underground geological formations.. These criteria can then be categorized in groups. Multi-criteria assessment (MCA) appears to hold much potential as a useful tool for characterising and better understanding differences in stakeholder assessments of CCSCarbon dioxide Capture and Storage and its implications, and for identifying options around which greater consensus on the desirability (or otherwise) of CCSCarbon dioxide Capture and Storage as a mitigationThe process of reducing the impact of any failure strategy might emerge (Gough and Shackley, 20062006 - C. Gough and S. ShackleyTowards a Multi-Criteria Methodology for Assessment of Geological Carbon Storage Optionssee more). This method delivers a rich profile of the views and preferences of participants and thus enables 'mapping' key issues that will affect the prospects for further development. A similar method is the Multi-Attribute Utility Theory (MAUT). The main difference between MAUT and MCA is that MAUT assumes a dependency of preferences of criteria, enabling the inclusion of subjective elements (Scholz and Tietje, 20022002 - R. W. Scholz and O. TietjeEmbedded Case Study Methods: Integrating Quantitative and Qualitative Knowledgesee more; Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
The Evidence Support Logic (ESL) has been designed to identify the amount of uncertainty or conflict involved in a decision. This involves systematically breaking down the question under consideration into a logical hypothetic model whose elements expose basic judgements and opinions related to the quality of evidence associated with a particular interpretation or proposition. A decision-support tool called TESLA implements Evidence Support Logic (ESL). The method involves constructing decision trees to reflect: (1) the Performance Assessment's context since decision depends on the storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere project's stage of development and the aims of the stakeholders); (2) the FEPs that may influence the system being evaluated; (3) the kinds of information that enable assessments about the characteristics and effects of interactions among these FEPs. The decision tree consists of a hierarchy of hypotheses, which links the main hypothesis of interest (e.g. insignificant CO2Carbon dioxide leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column from a deep storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids) to data or information (e.g. geological evidence for the existence of a cap rock, experimental evidence for the effective sealing of boreholes, output from supporting modelling studies etc). The 'evidence' for or against each hypothesis is the extent to which information leads to confidence in the hypothesis' dependability or falsehood respectively (Metcalfe et al., 20092009 - R. Metcalfe, P. Maul, S. Benbow, C. Watson, D. Hodgkinson, L. Paulley, R. Limer, R. Walke and D. SavageA unified approach to Performance Assessment of geological CO2 storagesee more). The 'evidence' may correspond to quantitative information (e.g. numerical model output, measurements in boreholes etc) or qualitative information (e.g. anecdotal evidence that a particular kind of borehole sealAn impermeable rock that forms a barrier above and around a reservoir such that fluids are held in the reservoir is effective). Each item of qualitative or quantitative information is then mapped into two values on a numerical scale of 0 to 1 representing evidence for and against. This representation of evidence is a type of Interval Probability Theory, which employs three-value logic. Experts assign values to each hypothesis representing the amount of supporting evidence, the amount of refuting evidence and the amount of uncertainty or conflict in the evidence. (Metcalfe et al., 20092009 - R. Metcalfe, P. Maul, S. Benbow, C. Watson, D. Hodgkinson, L. Paulley, R. Limer, R. Walke and D. SavageA unified approach to Performance Assessment of geological CO2 storagesee more; Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more).
The Method Organized for a Systematic Analysis of RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event (MOSAR) allows the analysis of the technical risks of a system and then identifies the prevention means in order to neutralize them. It consists of two main steps (Fig. 6-5). First step, 'A', allows the analysis of major risks. Second step 'B' makes a detailed analysis of project implementation and specifically defines the safety tools related to the technical dysfunction (all dysfunctions are found with this step). The MOSAR method is a systematic method which relies on a step by step method, in which no step can be neglected. This does not prevent flexibility: when an unexpected event arises or a new danger sourceAny process, activity or mechanism that releases a greenhouse gas, an aerosol, or a precursor thereof into the atmosphere appears, it can included at the beginning of the method without changing all the process. This method is built level by level where each level gives a specific information so that it is possible to stop at a chosen level. Unexpected events, such as physical harm and material, fauna, flora, ground and economic damages or unpleasant effects on the population, are defined. MOSAR is based on site observations and facts and is applicable to a specific installation because it accounts for technical aspects, site morphology and geology, politics, and economic and social aspects into account. It presents the advantage of creating improbable and unforeseeable riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event Scenarios with a first analysis, but whose implementation can be extremely beneficial. The important subjectivity of MOSAR has been noticed and this should be viewed as a strong point and not as a hindrance (Cherkaoui and Lopez, 20092009 - A. Cherkaoui and P. LopezCO2 Storage Risk Assessment: feasibility study of the systemic method MOSARsee more).
| 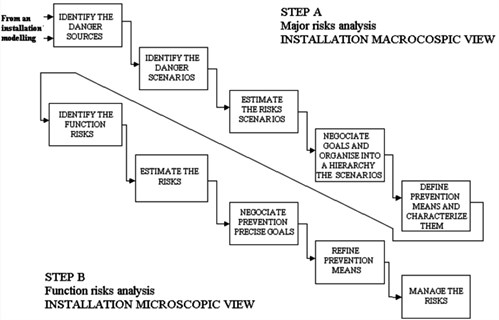
Fig. 6-5: The MOSAR method: Steps A and B (Cherkaoui and Lopez, 20092009 - A. Cherkaoui and P. LopezCO2 Storage Risk Assessment: feasibility study of the systemic method MOSARsee more). |
The Performance and RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event (P&R) assessment (or Performance and RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event Management methodology - P&RTM), for wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids integrity was developed by Schlumberger and OXAND. The uncertainties of the system are converted into the notion of probability and the quantity of CO2Carbon dioxide leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column mass assessed into the notion of severity. It also includes the definition of a RiskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event Acceptance Limit (RAL), which brings forwards the criteria of unacceptable risks. The methodology is based on experience in material ageing and riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event of complex systems, where probabilistic simulations are performed. It accounts for all stakes involved in wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids integrity management and enables the full integration of uncertainties as part of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event estimation. The methodology improves common approaches based on FEPs as it quantifies riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event levels. It provides useful and reliable tools to support decisions for wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids integrity management strategies or emergency plans. Updating riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event with incoming data allows an evolving vision of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event levels to optimize interventions in time. The main objectives of the riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event-based methodology regarding wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids integrity are to identify and quantify risks associated with CO2Carbon dioxide leakages along wells over time (from tens to thousands of years), to evaluate risks and to propose relevant actions to reduce unacceptable Risks (Le Guen et al., 20082009 - Y. Le Guen, V. Meyer, O. Poupard, E. Houdu and R. ChammasA Risk-Based Approach for Well Integrity Management over Long Term in a CO2 Geological Storage Projectsee more; Le Guen et al., 20092008 - Y. Le Guen, J. Le Gouevec, R. Chammas, B. Gerard, O. Poupard, A. Van Der Beken and L. JammesCO2 Storage - Managing the Risk Associated with Well Leakage over Long Timescalessee more; Condor et al., 20112011 - J. Condor, D. Unatrakarn, M. Wilson and K. AsghariA Comparative Analysis of Risk Assessment Methodologies for the Geologic Storage of Carbon Dioxidesee more)
A hybrid system-process model CO2Carbon dioxide-PENS (Predicting Engineered Natural Systems) is a probabilistic simulation tool designed to incorporate CO2Carbon dioxide injectionThe process of using pressure to force fluids down wells and sequestration knowledge from the petroleum industry to perform riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event of sites. It includes economic tools, as wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids as models for the physical and chemical interactions of CO2Carbon dioxide in a geological reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids (Viswanathan et al., 2008; Stauffer et al., 2009). This model is based on a PID (Process Influence Diagram)-like approach extending the FEPs analysis. The CO2Carbon dioxide-PENS tool aims at integrating in a system-level model a number of process-level models representing the storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids, the cap rock, the potential release mechanisms, the transport of CO2Carbon dioxide from the reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids and the release of CO2Carbon dioxide in surface.The CO2Carbon dioxide-PENS system model allows both a simplified analytical description of processes and the use of detailed processmodels. It links high level system models (i.e., reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids model) to the process level (wellboreThe physical hole that makes up the well, it can be cased, open, or a combination of both; open means open for fluid migration laterally between the wellbore and surrounding formations; cased means closing of the wellbore to avoid such migration leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column, chemical interaction of CO2Carbon dioxide) and represents thus a hybrid coupled process and system model designed to simulate CO2Carbon dioxide pathways, such as captureThe separation of carbon dioxide from other gases before it is emitted to the atmosphere, transport, injectionThe process of using pressure to force fluids down wells into geological reservoirs, potential leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column from the reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids and migrationThe movement of fluids in reservoir rocks of escaped CO2Carbon dioxide. Due to its modular architecture, the tool allows incorporation of additional process models by linking to dynamic linked libraries (DLL) and coupling of the wellManmade hole drilled into the earth to produce liquids or gases, or to allow the injection of fluids leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column module with the atmospheric model is feasible. At each time step in the system model, the wellboreThe physical hole that makes up the well, it can be cased, open, or a combination of both; open means open for fluid migration laterally between the wellbore and surrounding formations; cased means closing of the wellbore to avoid such migration module is queried to predict the leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column rate into the top aquiferAn underground layer of fluid-bearing permeable rock or unconsolidated materials (gravel, sand, or silt) with significant permeability to allow flow. Simulation of wellboreThe physical hole that makes up the well, it can be cased, open, or a combination of both; open means open for fluid migration laterally between the wellbore and surrounding formations; cased means closing of the wellbore to avoid such migration leakage(in CO2 storage) The escape of injected fluid from the storage formation to the atmosphere or water column is complicated and simulation approaches require PDFs with respect to potential failure mechanisms as input parameters to take account of uncertainties. CO2Carbon dioxide-PENS is being used inrisk assessments for several of the field tests and demonstrations being conducted as part of the United States Department of Energy's (US DOE's) Regional Carbon Sequestration Partnership efforts (CSLF, 20092009 - CSLFPhase I Final Report from CSLF Risk Assessment Task Forcesee more).
The System Modelling Approach (SMA) is part of the CO2Carbon dioxide-PENS and was developed in Los Alamos National Laboratory and originally designed to perform probabilistic simulations for the whole CCSCarbon dioxide Capture and Storage chain. The long-term fate of the injected CO2Carbon dioxide, including possible migrationThe movement of fluids in reservoir rocks patterns out of the target formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it, is simulated through probability distributions (Stauffer et al., 2009). Oldenburg and Bryant, 2007 decompose the system into process-level models. They focus on a simple certificationIn the context of carbon tradingA market-based approach that allows those with excess emissions to trade that excess for reduced emissions elsewhere, certifying that a project achieves a quantified reduction in emissions over a given period framework. The storage(CO2Carbon dioxide) A process for retaining captured CO2Carbon dioxide, so that it does not reach the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) complex is divided into compartments. The likelihood of a leak is evaluated by estimating the probability that a leakage(in CO2Carbon dioxide storage) The escape of injected fluid from the storage formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it to the atmosphereThe layer of gases surrounding the earth; the gases are mainly nitrogen (78%) and oxygen (around 21%) or water column pathway encounters the CO2Carbon dioxide plumeDispersing volume of CO2Carbon dioxide-rich phase contained in target formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it on the one side, and a target on the other side. The CO2Carbon dioxide flux across the pathway is simulated through deterministic simplified models, and the impacts of the release compared to acceptable thresholds. A level of riskConcept that denotes the product of the probability of a hazard and the subsequent consequence of the associated event is obtained by the product of the values of the probability and the consequences (CSLF, 20092009 - CSLFPhase I Final Report from CSLF Risk Assessment Task Forcesee more).
Researchers for the Weyburn CO2Carbon dioxide MonitoringMeasurement and surveillance activities necessary for ensuring safe and reliable operation of a CGS project (storage integrity), and for estimating emission reductions and Storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere Project have developed a program called CQUESTRA (CQ-1) and applied it to components of the project (Whittaker et al., 20042004 - S. Whittaker, D. White, D. Law and R. ChalaturnykIEA GHG Weyburn CO2 Monitoring & Storage Project Summary Report 2000-2004see more). The probabilistic conceptual model (PCM) consists of two components: the model domain, which defines the geologic setting, and the model processes, which include the physical and chemical processes that define CO2Carbon dioxide mass transport and storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere. The model domain is divided into four broad areas: the biosphere, the upper geosphereThe earth, its rocks and minerals, and its waters (all aquifers and aquitards above the reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids), the wells, and the lower geosphereThe earth, its rocks and minerals, and its waters (reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids and the aquifers and aquitards below the cap rock). Local variability in formationA body of rock of considerable extent with distinctive characteristics that allow geologists to map, describe, and name it porosityMeasure for the amount of pore space in a rock, permeabilityAbility to flow or transmit fluids through a porous solid such as rock, Darcy flow velocity, etc., is incorporated into Probability Distribution Functions (PDFs) to captureThe separation of carbon dioxide from other gases before it is emitted to the atmosphere the uncertainty in the PCM's domain features and processes. Once the physical PCM domain is fully described, CQ-1 quantifies the main driving forces relevant to the storage(CO2) A process for retaining captured CO2, so that it does not reach the atmosphere of CO2Carbon dioxide in a reservoirA subsurface body of rock with sufficient porosity and permeability to store and transmit fluids. CQ-1 was used to model the Weyburn system for a period of 5,000 years after completion(well) Refers to the cementing and perforating of casing and stimulation to connect a well bore to reservoir of EOREnhanced Oil Recovery: the recovery of oil additional to that produced naturally, achieved by fluid injection or other means CO2Carbon dioxide injectionThe process of using pressure to force fluids down wells. A Monte CarloA modelling technique in which the statistical properties of outcomes are tested by random inputs simulation method was used to sample the probability distribution functions for the CQ-1 input parameters (Deel et al., 20072007 - D. Deel, K. Mahajan, C. Mahoney, H. McIlvried and R. SrivastavaRisk Assessment and Management for Long-Term Storage of CO2 in Geologic Formations - United States Department of Energy R&Dsee more).